https://www.udemy.com/aws-certified-solutions-architect-associate/learn/v4/t/lecture/2050704?start=0
This section is essential regardless of the exam you’re taking.
- A VPC is a logical datacenter.’
- VPCs do NOT span Regions, but can span AZ
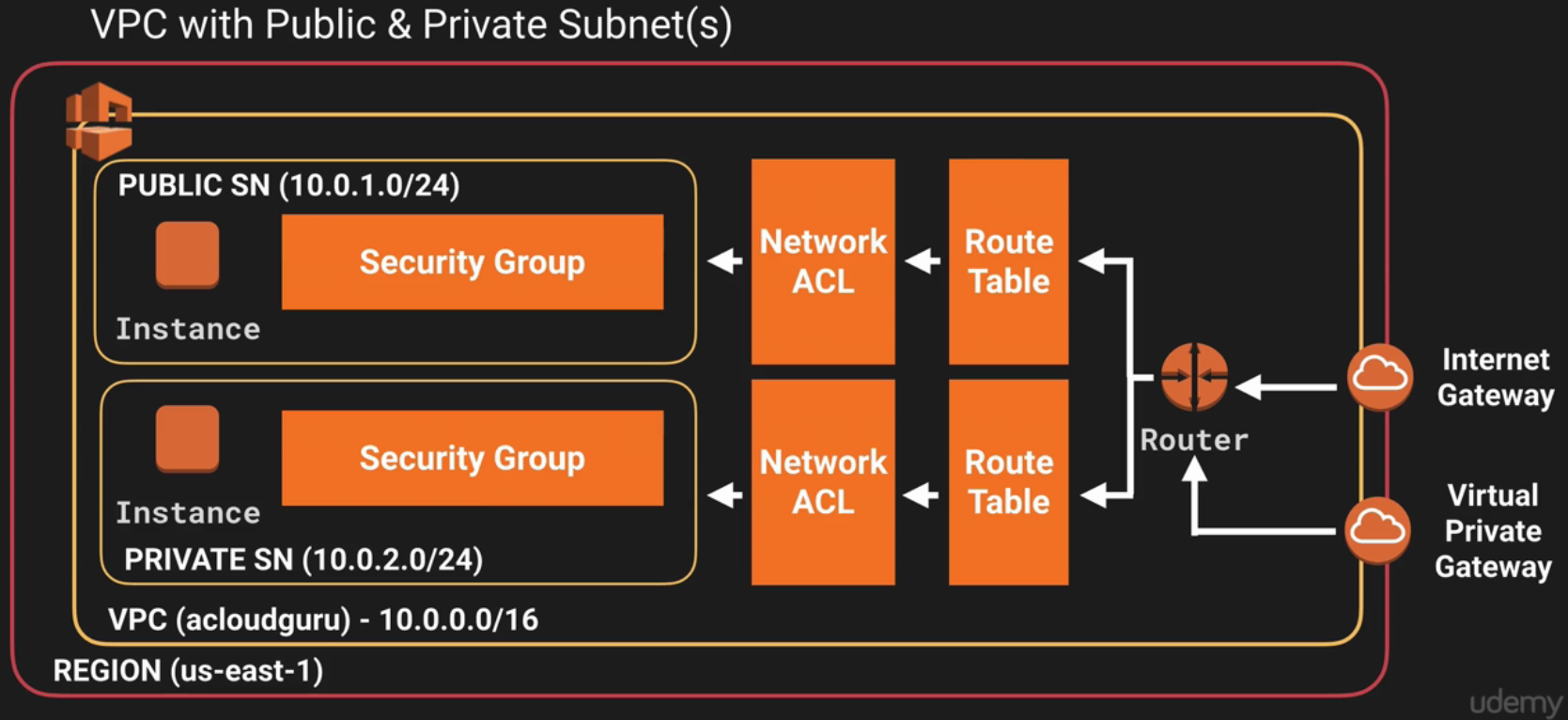
Amazon Virtual Private Cloud (Amazon VPC) lets you provision a logically isolated section of the Amazon Web Services (AWS) Cloud where you can launch AWS resources in a virtual network that you define. You have complete control over your virtual networking environment, including selection of your own IP address range, creation of subnets and configuration of route tables and network gateways.
You can easily customize the network configuration for your VPC. For example, you can create a public-facing subnet for your web servers that has access to the Internet, and place your backend system such as databases or application servers in a private facing subnet with NO Internet access. You can leverage multiple layers of security, including security groups and network access control lists, to help control access to EC2 instances in each subnet.
Additionally, you can create a Hardware VPN connection between your corporate datacenter and your VPC and leverage the AWS cloud as an extension of your corporate datacenter. (Hybrid Cloud)
Private Address Ranges
- 10.0.0.0 – 10.255.255.255 (10.0.0.0/8) – Corporate
- 172.16.0.0 – 172.31.255.255 (172.16.0.0/12)
- 192.168.0.0 – 192.168.255.255 (192.168.0.0/16) – Home Networking
- Red Outline defines our Region
- Yellow line defines the VPC
- 10.0.0.0/16 (Private Network Address)
- Highest available from AWS is /16
- One Subnet ALWAYS = 1 Availability Zone!
- Subnets cannot span Availability Zones!
- Security Groups, Network ACLs and Route Tables can span multiple Subnets (Multiple AZs)
What can you do with a VPC?
- Launch instances into a subnet of your choosing that can be Public or Private
- Assign custom IP address ranges in each subnet.
- Configure route tables between subnets
- Create an Internet gateway and attach it to our VPC
- You can only create 1 Internet Gateway per VPC
- Much better security control over your AWS resources
- Instance security groups.
- These are stateful, so if HTTP is allowed IN, it is also allowed OUT
- Subnet Access Control Lists are Stateless, so if you allow HTTP IN, you must also create a rule allowing it OUT.
Default VPCs vs. Custom VPC
- Default VPC is user friendly, allowing you to immediately deploy instances
- All Subnets in a default VPC have a route out to the Internet.
- Each EC2 instance has both a public and private IP address.
- If you delete the default VPC, the only way to get it back is to contact AWS.
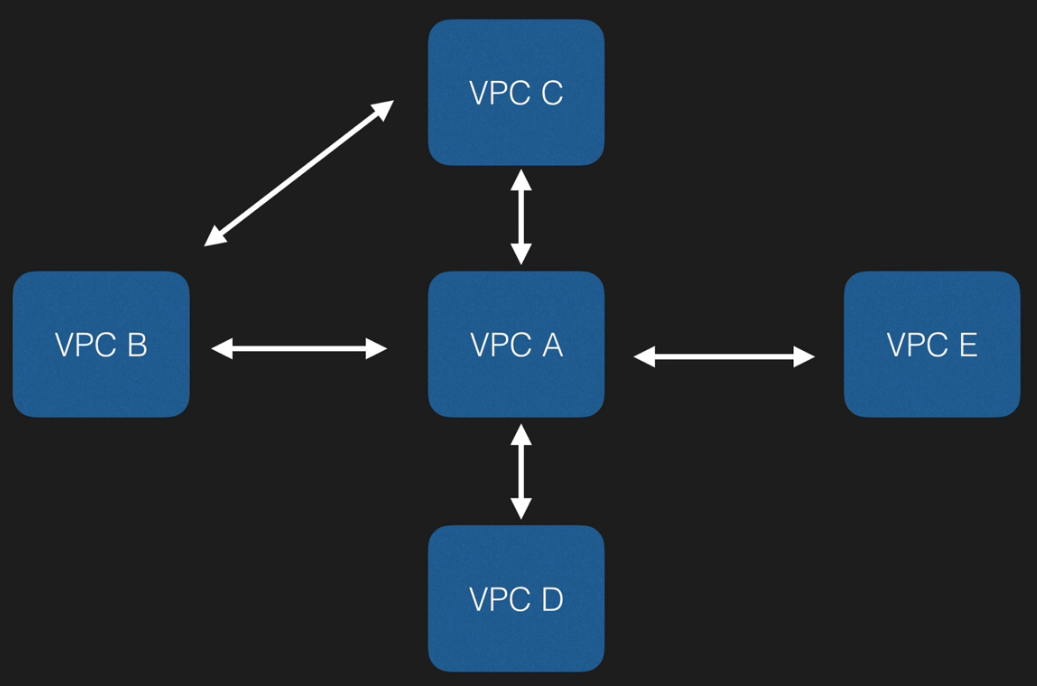
VPC Peering
- Allows you to connect one VPC with another via a direct network route using private IP addresses.
- Instances behave as if they were on the same private network
- You can peer VPCs with other AWS accounts as well as with other VPCs in the same account.
- Peering is in a star configuration, i.e. 1 central VPC Peers with 4 others. NO TRANSITIVE PEERING!!!
- Example
- ‘A’ can peer into ‘B’, ‘C’, ‘D’ and ‘E’
- ‘B’ cannot peer into ‘C’ through ‘A’ (transitive)
- A new peering connection must be established specifically for ‘B’ to talk to ‘C’
Exam Tips
- Think of a VPC as a logical datacenter in AWS
- Consists of Internet Gateways (IGWs, aka Virtual Private Gateways), Route Tables, Network Access Control Lists, Subnets and Security Groups.
- 1 Subnet = 1 Availability Zones
- Security Groups are Stateful, Network Access Control Lists are Stateless
- No Transitive Peering!
- Peering can be between different accounts!
- Need to be able to set these up by memory!
What we did
- Created a VPC
- Defined IP address range: 10.0.0.0/16
- By default this created a Network ACL and Route Table
- Created a custom Route Table
- Created 3 subnets
- Created Internet Gateway
- Attached to our customer route
- Adjusted Public subnet to use the IGW
- Provisioned and EC2 instance with an Elastic IP address
- EC2s MUST have either an Elastic IP or Elastic Load Balancer to access the Internet!