Overview
- Security Architecture and Design
- Common security models
- Architecture, design, virtualization, cloud and solutions
- How computers work and how the are logical segmented
- Threads to our applications, systems and devices
- Cryptography
- History of
- Types of encryption
- Hashes
- Cryptography attacks
- Digital signatures
- Physical Security
- Site and facility secure design principles
- Perimiter defense
- HVAC, Power and fire suppression
S9 – Security models and concepts
Security Models Fundamental Concepts
Types of Security Models
- DAC (Discretionary Access Control)
- Gives subjects full control of objects they have created or been given access to
- MAC (Mandatory Access Control)
- System enforced access control based on a subject’s clearance and an object’s labels
- RBAC (Role Based Access Control)
- Access to objects is granted based on the role of the subject.
- ABAC (Attribute Based Access Control)
- Access to objects is granted based on the subjects, objects and environmental conditions
- Attributes could be:
- Subject (user) – Name, role, ID, clearance, etc.
- Object (resource) – Name, owner, date of creation
- Environment – Location and or time of access, and threat levels.
- RUBAC (Rule Based Access Control)
- Access is granted based on If/Then statements
Security Model Examples
Exam Topic!
Bell-LaPadula: (MAC / Confidentiality)
- Simple Security property “No Read UP”
- Subjects with Secret clearance can’t read Top Secret data.
- * Security Property: “No Write DOWN”
- Subjects with Top Secret clearance can’t write Top Secret information to Secret folders.
- Strong * Property: “No Read or Write UP and DOWN”
- Subjects can ONLY access data on their own level.
BIBA: (MAC / Integrity)
- Simple Integrity Axiom: “No Read DOWN”
- Subjects with Top Secret clearance cannot read Secret data.
- Integrity is the purpose here. He don’t want to have wrong or lacking lower clearance level data confuse us.
- * Integrity Axiom: “No Write UP”
- Subjects with Secret clearance can’t write Secret information to Top Secret folders
- We don’t want wrong or lacking lower level information to propagate to a higher level.
- Invocation Property: No Read or Write UP”
- Subjects can never access or alter data on a higher level.
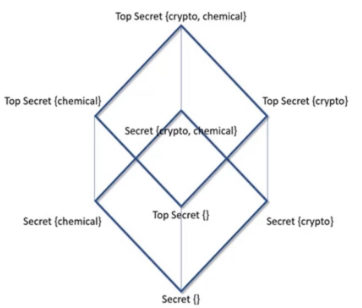
Lattice Based Access Control [LBAC] (MAC)
- A subject can have multiple access rights.
- A subject with Top Secret {crypto, chemical} would be able to access everything in this lattice.
- A subject with Secret {crypto} would only have access to that level.
- A subject with Top Secret {chemical} would have access to only {chemical} in Top Secret and Secret.
5:30