Understanding the Dangers of Wireless Networks
- Wardriving: Driving around an area looking for open networks.
- Hackers: People looking to steal information or simply perform malicious behavior.
- Employees: Companies that block Wi-Fi trying to create security, but employees create their own to enable wi-fi functionality.
Wireless Security
Authentication
- Require Username and Password
- May limit to specific devices
- May require device to present a authentication certificate
Encryption
- Everything sent over the network will be encrypted and scrambled
Intrusion Prevention System (IPS)
- Used to detect rogue wireless access systems
- Will shutdown switchport it is connected to and/or
- Notify System Admin of the system.
Encryption and Authentication Combinations
Originally: Pre-shared Key WEP (bad)
- Key is created on WAP (Wireless Access Point) and shared with users (Like a password).
- Several known attacks to break through encryption keys.
- Ex-employees would retain key or entire company would need to “re-key” with personnel changes.
- Pre-shared keys should be rotated on a monthly basis.
Evolution #1: Pre-shared Key WPA (WPA1)
- Interim solution that used existing hardware.
- Uses encryption TKIP – much better
Evolution #2: WPA(1) and 802.1x Authentication
- 802.1x is a standard for authenticating who you are.
- Device would pass USERNAME and PASSWORD to access point.
- Access Point would check these against a control server that would confirm or deny.
- Access Point and Device will then generate a set of encryption keys for the session.
Evolution #3: WPA2 (802.11i) and 802.1x
- WPA2 became 802.11i standard
- Encryption method known as AES
- Can be combined with Authentication for perfect security.
- Still allows WPA1 PSK (Pre-shared Keys)
Understanding the Service Set Identifier (SSID )
The SSID:
- Uniquely identifies and separates wireless networks
- Essentially your Network Name
When a Wireless Client is enabled:
- Client issues a probe: “Hey, who’s out there?”
- Access Point(s) respond with a beacon: “I’m here, my name is Public”
- Client associates with chosen SSID
- Access Point adds client MAC to Association Table
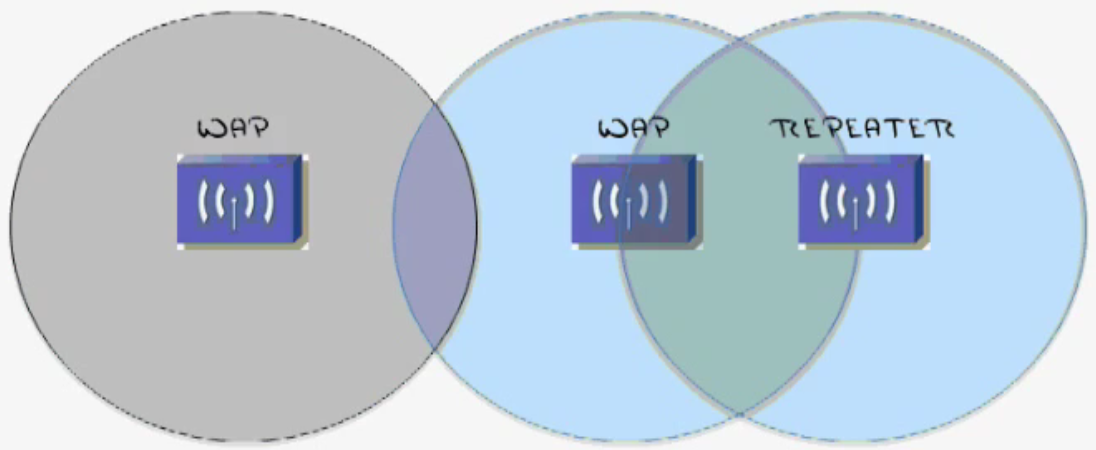
Correct Design of a WLAN
- RF Service areas should have 10% – 15% overlap. (Can use a sniffer program to tell you how strong a signal is.)
- Repeaters should have 50% overlap. (Will take an existing signal and “extend” it)
- Bordering Access Points should use different channels. (In example above from Left to Right: Channel 1, 6, 11)
Understanding the Terms
- Basic Service Set (BSS): A single access point and its service (coverage) area. (Left example)
- Extended Service Set (ESS): Two or more BSS (Full Network above)
- Roaming: Client moves between BSS without dropping connection only possible with Extended Service Sets.
Setting Up a Wireless Network
- Pretest switch port with laptop (DHCP, DNHS, etc.)
- Connect WAP (Wireless Access Point)
- Setup and test ssid with no security
- Add and test security (Pre-shared Key (WEP, WEP2))
- Add and test Authentication (802.1x) [Using Server with Usernames and Passwords]