https://www.udemy.com/aws-certified-solutions-architect-associate/learn/v4/t/lecture/7719220?start=0
Grants users limited and temporary access to AWS resources. Users can come from three sources:
- Federation (typically Active Directory)
- Uses Security Assertion Markup Language (SAML)
- Grants temporary access based off the users Active Directory credentials.
- Does not need to be a user in IAM
- Single Sing On allows users to log in to AWS console without assigning IAM credentials
- Federation with Mobile Apps
- Facebook/Amazon/Google or other OpenID providers to log in
- Cross Account Access
- Allows users from one AWS account access resources in another.
Understanding the Key Terms
- Federation
- Combining or joining a list of users in one domain (such as IAM) with a list of users in another domain (such as Active Directory, Facebook, etc.)
- Identity Broker
- A service that allows you to take an identity from point A and join it (federate it) to point B
- Identity Store
- Service like Active Directory, Facebook, Google, etc.
- Identities
- A user of a service like Facebook, etc.
- User accounts
- A user of a service like Facebook, etc.
Scenario
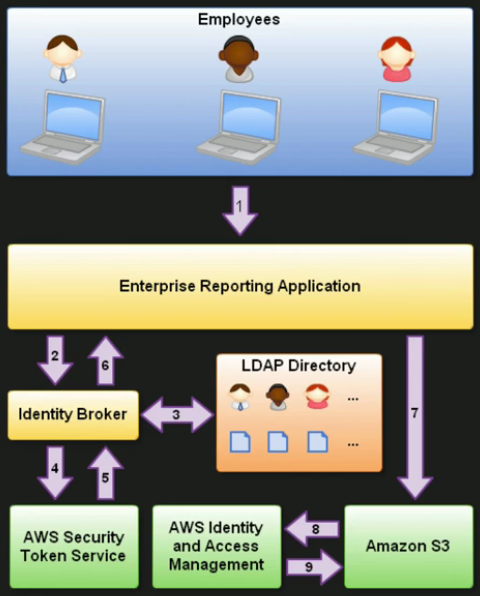
You are hosting a company website on some EC2 web servers in your VPC. Users of the website must log in to the site which then authenticates against the companies active directory servers which are based on site at the companies head quarters.
Your VPC is connected to your company HQ via a secure IPSEC VPN. Once logged in, the user can only have access to their own S3 bucket. How do you set this up?
- User logs in
- Information is passed to an Identity Broker
- Identity Broker looks for user in LDAP
- Identity Broker initiates a call to the Security Token Service
- GetFederationToken()
- Uses IAM Credentials
- IAM Policy
- Duration (1 to 36 hours)
- STS returns the following (Important)
- Access Key
- Secret Access Key
- Token
- Duration (This is the Token’s lifetime)
- These are then returned to the Reporting Application (Where the user initially logged in)
- Reporting App attempts to connect to S3
- S3 checks IAM to see if the Token is legit
- IAM replies Yes, and the user is granted access.
Exam Tips
- Develop an Identity Broker to communicate with LDAP and AWS STS
- Identity Broker always communicates with LDAP first, the with STS
- Application then gets temporary access to AWS resources