Lesson 2 of 6
Main Menu
Overview of AD DS
- Protocol
- Lightweight Directory Access Protocol (LDAP)
- X.500 Standard
- Based on TCP/IP
- A method for accessing, searching and modifying a directory service
- A client-server model
- Lightweight Directory Access Protocol (LDAP)
- Authentication (Who you are)
- Authentication is the process of verifying a user’s identity on a network
- Authentication includes 2 components
- Interactive Logon: Grants access to the local computer
- Network Authentication: Grants access to network resources
- Authorization (What you can do)
- Authorization is a process of verifying that an authenticated user has permissions to perform an action
- Security principals are issued Security Identifiers (SIDs) when the account is created
- User accounts are issued security tokens during authentication that include the user’s SID and all related group SIDs
- Security Token=This is who I am, these are the groups I belong to.
- Shared resources on a network include access control lists (ACL) that define who can access the resource.
- The Security Token is compared against the Discretionary Access Control List (DACL) on the resource and access is granted or denied.
- Write, Read, Change
- Authorization is a process of verifying that an authenticated user has permissions to perform an action
- Why Deploy AD DS
- AD DS?
- AD DS provides a centralized system for managing users, computers and other resources on a network.
- These features include:
- Centralized Directory
- Instead of granting access on 5 computers to 5 users, AD lets you create all of those accounts in 1 place.
- Those users can now log into anyone of those computers at any time with the same username/password
- Integrated Security
- Scalability
- It is only limited by the abilities of your Domain Controllers
- Common Management interface.
- AD DS?
- Centralized Network Management
- AD DS centralizes network management by providing
- Single location and set of tools for managing user and group accounts.
- Single location for assigning access to shared network resources
- Directory service for AD DS enabled applications
- Example: Exchange can get information about users it would not normally have.
- Options for configuring security policies that apply to all users and computers
- aka Group Policy – not going to deep dive in this course.
- Group policies to manage user desktops and security settings
- AD DS centralizes network management by providing
- Requirements for Installing AD DS
- TCP/IP
- Configure appropriate TCP/IP and DNS server addresses.
- Credentials
- To install a new AD DS forest, you need local Administrator access on the server.
- To install an additional domain controller in an existing domain, you need to be a member of the Domain Admins group.
- Domain Name System (DNS) Infrastructure
- Verify that a DNS infrastructure is in place. When you install AD DS, you can include DNS server installation if it is needed.
- When you create a new domain, a DNS delegation is created automatically during the installation process. Creating a DNS delegation requires credentials that have permissions to update the parent DNS zones.
- TCP/IP
- Overvew of AD DS and DNS
- AD DS requires a DNS infrastructure
- AD DS domain names must be DNS domain names (FQDN)
- AD DS domain controller records (SRV records) must be registered in DNS to enable other domain controllers and client computers to locate the domain controllers.
- Happens automatically
- DNS zones can be stored in AD DS as Active Directory integrated zones.
- Advanced feature
- Can use AD as replication mechanism for DNS
- As a security boundary for DNS
- Advanced feature
- Overview of AD DS Components
- AD DS is both physical and logical components
- Physical
- Data Store
- Domain Controllers
- Global catalog server
- Read-Only Domain Controller (RODC) (Optional)
- Supported by Windows Server 2008 and later
- Allows a copy of your domain to be placed in a branch office.
- Can read from and use the information, but no risk of being compromised.
- Logical Components
- Partitions
- Schema
- Domains
- Domain Trees
- Forests
- Sites
- Organizational Units (OUs)
AD DA Physical Components
- Domain Controllers
- A domain controller is a server with AD Ds server role installed that has specifically been promoted to a domain controller
- Host a copy of the AD DS directory store
- Provide authentication and authorization services
- Replicate updates to other domain controllers in the domain and forest
- Allow administrative access to manage user accounts and network resources in a central location
- Global Catalog Servers
- Global catalog servers are domain controllers that also store a copy of the global catalog
- Contains a copy of all AD DS objects in a forest that includes only some of the attributes of each object in the forest
- Improves efficiency of object searches by avoiding unnecessary referrals to domain controllers
- Required for users to log on to a domain
- Data Store
- The AD DS data store is where all this information is physically kept on a server. The data store contains the database files and processes that store and manage directory information for users, services and applications.
- Contains the Ntds.dit file
- Everything is in this file????
- Is stored by default in the %SystemRoot%\NDTS filder on all domain controllers
- Is accessible only through the domain controller processes and protocols.
- Replication
- Replicates copies of all updates of the AD DS database to all other domain controllers in a domain or forest
- If a user is added/deleted, or a password is changed, etc. these changes are replicated across DCs.
- The AD DS replication topology is created automatically as new Domain Controllers are added to the domain.
- This can be modified using sites.
- Ensures that all domain controllers have the same information
- Uses a multi-master replication model
- No single point of failure or single source for information.
- All changes and change locations are recorded for audit purposes.
- Can be managed by creating AD DS sites.
- Replicates copies of all updates of the AD DS database to all other domain controllers in a domain or forest
- Sites
- An AD DS site is used to represent a network segment where all domain controllers are connected by a fast and reliable network connection.
- Associated with IP subnets
- Used to manage replication traffic
- Used to manage client logon traffic
- Used by site aware applications such as Distributed File Systems (DFS) or Exchange Server
- Used to assign group policy objects to all users and computers in a company location
- Sites are defined based on network bandwidth
AD DS Logical Components
- AD DS Schema
- Defines every type of object that can be stored in the directory
- Enforces rules regarding object creation and configuration
- Object Types
- Class Object: What objects can be created in the directory
- Users
- Computers
- Attribute Objects: Information that can be attached to an Object (Metadata?)
- Display Name
- User Name
- Computer Name
- Phone number
- Class Object: What objects can be created in the directory
- The Basics
- Domains are used to group and manage objects in an organization
- An administrative boundary for applying policies to groups of objects
- A replication boundary for replicating data between domain controllers
- An authentication and authorization boundary that provides a way to limit the scope of access to resources.
- Trees
- A domain tree is a hierarchy of domains in AD DS
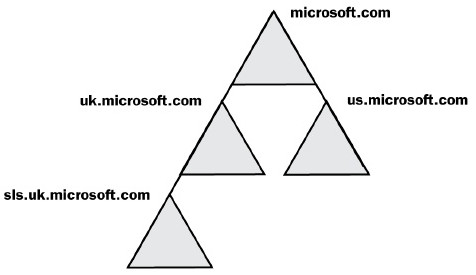
- All domains in the tree:
- Share a contiguous name space with the parent domain
- Can have additional child domains
- By default create a two-way transitive trust with other domains.
- Any resources in any of these domains can be accessed by accounts in those domains.
- No special rules for users in sls.uk.microsoft.com to access resources in us.microsoft.com
- Any resources in any of these domains can be accessed by accounts in those domains.
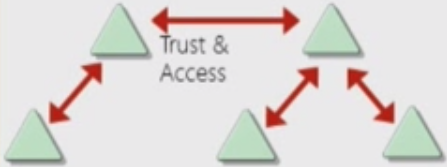
- Forests
- A forest is a collection of one or more Domain Trees.
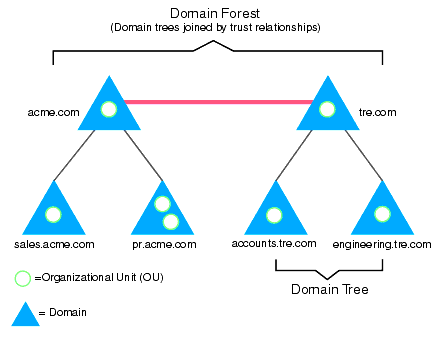
- Share a common schema
- Definition of Objects and Attributes is the same.
- Share a common configuration partition
- Share a common global catalog to enable searching
- These start to matter with Forests
- Any user in any tree in a given Forest can find any object by querying the Global Catalog.
- Enable trusts between all domains in the forest
- Automatic – trusts exists between all domains in all trees in a forest.
- Share the Enterprise Admins and Schema Admins group.
- These people can change anything in any domain or tree in the forest
- Domain admins are only admins for that domain.
- Organizational Units (OUs)
- Subdivision of a Domain?
- OUs are Active Directory containers that can contain users, groups, computers and other OUs
- OUs represent your organization hierarchically and/or logically
- Manage a collection of objects in a consistent way
- Manage objects that are consistent with each other, but not consistent with other objects
- Delegate permissions to administer groups of objects
- Apply policies (Group Policies)
- Domains are used to group and manage objects in an organization
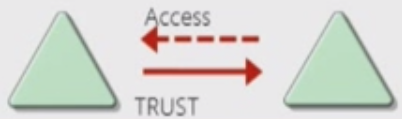
- Trusts
- Trusts provide a mechanizm for users to gain access to resources in another domain.
- All domains in a forest trust all other domains in the forest
- Trusts can extend outside of the forest (Manual process)
- Types of Trust
- Directional: The trust direction flows from the trusting domain to the trusted domain.
- Transitive: The trust relationship is extended beyond a two-domain trust to include other trusted domains. (Default Behavior)
- AD DS Objects
- Every THING is an object
- Any additional data that belongs to that Object is an Attribute (Metadata)
- Examples:
- Users: Enables network resource access for a user
- InetOrgPerson: Similar to a user, but used for compatibility with other directory services (X.500 Standard)
- Contacts: Used to assign Email address and other Attributes to external users that do not by default have network access.
- Groups: Used to simplify the administration of access control
- Computers: Enables authentication and auditing of computer access to resources
- Printers: Use to simplify the process of locating and connecting to printers
- Shared Folders: Enables users to search for shared folders based on properties.
- Every THING is an object
- Demo: Installation and Management