< Section 23 | Home | Section 25 >
76% Complete!
153. Introduction
https://www.udemy.com/course/cisco-icnd1/learn/lecture/8677024#content
154. Access Control Lists Overview
https://www.udemy.com/course/cisco-icnd1/learn/lecture/8677036#content
Access Control Lists
- Identifies traffic based on characteristics of the packet, such as source IP, Dest IP, port number
- The router or switch can take an action based on the result of the ACL
- ACLs are supported on both routers and switches (R/S).
ACLs for Security
- Original use of ACLs was as a security feature to decide if traffic should be allowed to pass through the R/S
- By default, an R/S will allow all traffic to pass between its interfaces
- When ACLs are applied, the R/S identifies the traffic and then decides if it will be allowed or not.
Other Uses
- ACLs are also used in other software policies when traffic has to be identified.
- Identify traffic to give better service to in an QoS Quality of Service policy
- Identify traffic to translate to a different IP address in a NAT Network Address Translation policy.
ACE Access Control Entries
- Access Control Lists are made up of Access Control Entries, which are a series of permit or deny rules
- Each ACE is written in a separate line
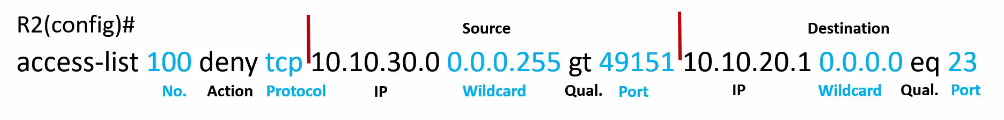
access-list Number Action Protocol SourceIP SourceWildCard SourceQualifier SourcePort DestIP DestWildCard DestQualifier DestPort
- The ACL is a series of these commands that form the list.
Note:
- Starting with Windows 7, outgoing port numbers start with 49152
- Previous versions started with 1024
155. Standard, Extended and Named ACLs
https://www.udemy.com/course/cisco-icnd1/learn/lecture/8677042#content
Standard vs Extended ACLs
- IP standard access list: 1 – 99
- IP extended access list: 100 – 199
- IP standard access list (expanded range): 1300 – 1999
- IP extended access list (expanded range): 2000 – 2699
- ! Truncated!
Standard vs Extended
- Standard ACLs only list the source IP address
- Extended ACLS also include
- Protocol (TCP/UDP/IPMC…)
- Destination address
- Port number
Standard Example
r1(config)# access-list 1 deny 10.10.10.10 0.0.0.0 r1(config)# access-list 1 permit 10.10.10.0 0.0.0.255
- The default wildcard mask for a Standard ACL is 0.0.0.0, meaning an idividual host address
- access-list 1 deny 10.10.10.10
- This is the same as ‘access-list deny 10.10.10.10 0.0.0.0’
- access-list 1 deny 10.10.10.10
- Do not forget to enter the wildcard when allowing/blocking an IP subnet
- access-list deny 10.10.10.0 0.0.0.255
Extended ACL Examples
- Extended ACLs DO NOT have a default wildcard mask!
r1(config)# access-list 100 deny tcp 10.10.10.10 0.0.0.0 gt 49151 10.10.50.10 0.0.0.0 eq 23 r1(config)# access-list 100 permit tcp 10.10.10.0 0.0.0.255 gt 49151 10.10.50.10 0.0.0.0 eq telnet
Named Access Lists
- Access Control Lists referenced by name start with `ip`
r1(config)# ip access-list <standard|extended> MyAclName r1(config-extended-nacl)# permit 10.10.10.0 0.0.0.255
156. ACL Syntax
https://www.udemy.com/course/cisco-icnd1/learn/lecture/8677048#content
Standard
r1(config)# access-list 1 ? deny Specify packets to reject permit Specify packets to forward remark Access list entry comment
Extended
r1(config)# access-list 100 ? deny Specify packets to reject dynamic Specify a DYNAMIC list of PERMITs or DENYs permit Specify packets to forward remark Access list entry comment r1-dhcp(config)#access-list 100 permit ? <0-255> An IP protocol number ahp Authentication Header Protocol eigrp Cisco's EIGRP routing protocol esp Encapsulation Security Payload gre Cisco's GRE tunneling icmp Internet Control Message Protocol igmp Internet Gateway Message Protocol ip Any Internet Protocol ipinip IP in IP tunneling nos KA9Q NOS compatible IP over IP tunneling object-group Service object group ospf OSPF routing protocol pcp Payload Compression Protocol pim Protocol Independent Multicast sctp Stream Control Transmission Protocol tcp Transmission Control Protocol udp User Datagram Protocol r1-dhcp(config)#access-list 100 permit tcp ? A.B.C.D Source address any Any source host host A single source host object-group Source network object group
ACL Definitions
Protocols
- TCP & UDP
- You can use a specific Port to restrict a specific application
- IP – All traffic. Includes UDP, TCP. ICMP, Network Discovery, Routing Information, etc.
Sources and Destinations
- Wildcards
- 0.0.0.0 = 255.255.255.255 subnet mask – aka, a specific IP address / host
- host IP.ADD.RE.SS = IP.ADD.RE.SS 0.0.0.0
- any
- any = 0.0.0.0 255.255.255.255
- 0.0.0.0 = 255.255.255.255 subnet mask – aka, a specific IP address / host
Port Numbers
Source
- any: match all ports (This is the default if not listed)
- eq X: port is exactly ‘X’
- gt/lt X: Match packets with a port greater than / less than ‘X’
- range: Match ports within the range specified
- neq X: Not Equal. Port does not match ‘X’
Destination
Destination ports have well known port numbers built in.
- eq www, eq telnet, eq dns, etc
Logging
- To log a packet request that attempts to break an ACL rule, suffix the rule with the word ‘log’
- Logging is for an external server or something – INCOMPLETE
access-list 100 deny tcp host 10.10.10.10 10.10.20.0 0.0.0.255 eq ssh log LOG-NAME?
Troubleshooting
show access-lists
- These commands will also show you how many log entries matched the rules.
- By ‘match’, it means the traffic was permitted or denied according to the rule.
- If you are expecting traffic to flow, but you do not see the count incrementing, it is likely being blocked/prevented somewhere else. (connectivity? switchport down?)
- ‘Log’ keyword is NOT required for these counters.
#show access-list #show access-list 100 Extended IP access list 100 deny tcp host 10.10.10.10 10.10.20.0 0.0.0.0 eq ssh (13 match(es))
157. ACL Operations
https://www.udemy.com/course/cisco-icnd1/learn/lecture/8677060#overview
- ACLs are applied at the Interface Level with the Access-Group command
- ACLS can be applied in the Inbound or Outbound direction
- You can have a maximum of one ACL per interface per direction
- You can have both an inbound and outbound ACL on the same interface
- You cannot have 2 ACLs on one interface with both Inbound or both Outbound
- An Interface can have
- No ACLs
- 1 Inbound
- 1 Outboud
- 1 Inbound and 1 Outbound
Access Group Configuration
r1(config)# interface f0/1 r1(config-if)# ip access-group 100 out r1(config-if)# ip access-group 101 in
ACL Show Commands
show running-config show ip interface f0/1 | include access list show access-lists show access-lists 110
Access Control Entry Order
- The order of rules are important!
- ACLs are read from top to bottom
- As soon as a rule matches the packet, the permit or deny action is applied and the ACL is not processed any further.
Example: Deny 10.10.10.10 but permit the rest of 10.10.10.0/24
access-list 1 deny host 10.10.10.10 access-list 1 permit 10.10.10.0 0.0.0.255
Example: Permit all 10.10.10.0/24 including 10.10.10.10
access-list 1 permit 10.10.10.0 0.0.0.255 access-list 1 deny 10.10.10.1
ACEs (Access Control Entry) are automatically incremented by 10
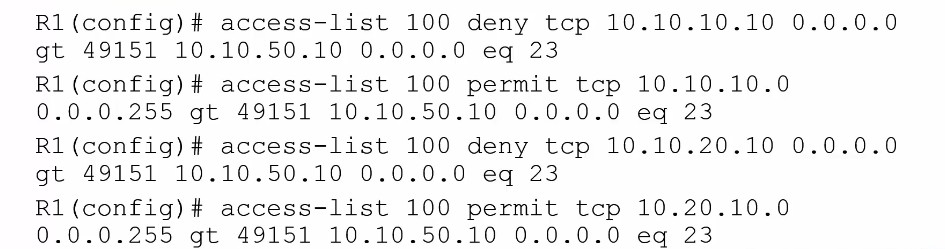
show access-lists 110 Extended IP access list 110 10 deny tcp host 10.10.10.10 host 10.10.50.10 eq telnet 20 permit tcp 10.10.10.0 0.0.0.255 host 10.10.50.10 eq telnet 30 deny tcp host 10.10.20.10 host 10.10.50.10 eq telnet 40 permit tcp 10.20.10.0 0.0.0.255 host 10.10.50.10 eq telnet
Injecting ACEs requires using Named ACL convention
- This was originally only allowed on named ACLs. but now works on Numbered as well
(config)# ip access-list extended 110 (config-ext-nacl)# 15 deny tcp host 10.10.10.11 host 10.10.50.10 eq telnet (config-ext-nacl)# end show access-lists 110 Extended IP access list 110 10 deny tcp host 10.10.10.10 host 10.10.50.10 eq telnet 15 deny tcp host 10.10.10.11 host 10.10.50.10 eq telnet 20 permit tcp 10.10.10.0 0.0.0.255 host 10.10.50.10 eq telnet 30 deny tcp host 10.10.20.10 host 10.10.50.10 eq telnet 40 permit tcp 10.20.10.0 0.0.0.255 host 10.10.50.10 eq telnet
Implicit Deny All
- There is an implicit ‘deny any any` rule at the bottom of ACLs
- If an ACL is not applied to an interface, all traffic is allowed.
- If an ACL is applied, all traffic is denied except what is explicityly allowed.
Example: Traffic from 10.10.10.0/24 is allowed, all other traffic is denied.
access-list 1 permit 10.10.10.0 0.0.0.255
Explicit Permit All
- You can override the implicity ‘Deny All’ by adding a Permit All line at the end of the ACL.
access-list 1 deny 10.10.10.0 0.0.0.255 access-list 1 permit any
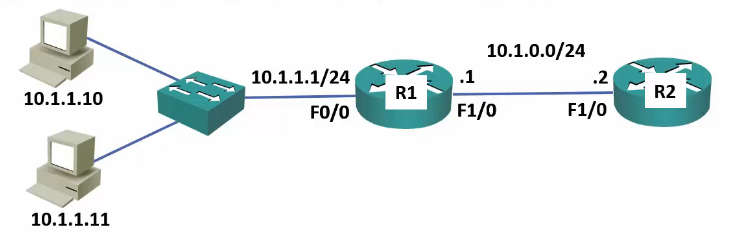
Traffic Sourced from Router
- ACLs applied to an interface DO NOT apply to traffic that originates from the router itself.
- The hosts in the 10.1.1.0/24 subnet cannot telnet to R2
- An Admin can telnet to R2 from the CLI on R1
(config)# access-list 100 deny tcp any any eq telnet (config)# int f1/0 (config-int)# ip access-group 100 out
158. Numbered ACLs Lab Demo
https://www.udemy.com/course/cisco-icnd1/learn/lecture/8677054#overview
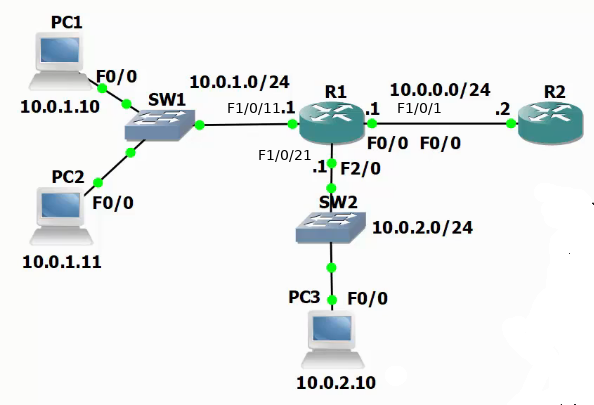
Inital Setup
- All PCs have connectivity everywhere.
- My lab has an additional 10.1.0.2/24 on R2 F0/1
R1# show ip route 10.0.0.0/8 is variably subnetted, 4 subnets, 2 masks C 10.0.2.0/24 is directly connected, FastEthernet1/0/21 C 10.0.0.0/24 is directly connected, FastEthernet1/0/1 S 10.1.0.0/16 [1/0] via 10.0.0.2 C 10.0.1.0/24 is directly connected, FastEthernet1/0/11
Example 1: PCs in 10.0.2.0/24 should not have connectivity to R2
Using a standard ACL
R1(config)# access-list 21 deny 10.0.2.0 0.0.0.255 R1(config)# access-list 21 permit 10.0.1.0 0.0.0.255 R1(config)# int f1/0/1 ip access-group 21 out
Test
PC3$ ping 10.0.0.2 PING 10.0.0.2 (10.0.0.2) 56(84) bytes of data. From 10.0.2.1 icmp_seq=1 Packet filtered From 10.0.2.1 icmp_seq=2 Packet filtered From 10.0.2.1 icmp_seq=3 Packet filtered PC1$ ping 10.0.0.2 PING 10.0.0.2 (10.0.0.2) 56(84) bytes of data. 64 bytes from 10.0.0.2: icmp_seq=1 ttl=254 time=1.13 ms 64 bytes from 10.0.0.2: icmp_seq=2 ttl=254 time=1.10 ms 64 bytes from 10.0.0.2: icmp_seq=3 ttl=254 time=1.10 ms
You Were Here ~8:00
Example 2: Permit telnet from PC1 to R2. All others denied.
R1(config)# access-list 100 permit tcp host 10.0.1.10 host 10.0.0.2 eq telnet R1(config)# access-list 100 deny tcp any host 10.0.0.2 eq telnet R1(config)# access-list 100 permit ip any any R1(config)# int f1/0/1 R1(config-if)#ip access-group 100 ou
159. Named ACLs Lab Demo
160. Packet Filters vs. Stateful Firewalls
161. Access Control Lists Configuration – Lab Exercise