< 7 Securing your Domain | Home | 9 Active Directory Backups >
34: Enabling Script Execution for Powershell
https://www.udemy.com/course/active-directory-group-policy-2012/learn/lecture/8301955#content
Issue: Run a script in Powershell and save it can cause an error.
- Start > Powershell ISE (Editor?) > Click dropdown to open editor pane.
- echo “Hello, World!” > Run Script (Play icon)
- File > Save As > \somefolder\somefilename
- Run again (This did not happen to me)
File C:\somefolder\somefilename cannot be loaded because running scripts is disabled on this system. for more information, see about_Execution_Policies at http://go.microsoft.com.....
Look for what might be blocking…
- rsop.msc
- Computer Config > Admin Templates > Windows Components > Windows Powershell > Turn on Script Execution > Disabled
- User Config > Admin Templates > Windows Components > Windows Powershell > Turn on Script Execution > Enabled
- Computer config has precedence!
Disable it
- Hint: Is in Default Domain Policy
- Comps > Policies > Admin Temps > Win Comps > Win Powershell > Turn on script execution > Not configured
- Users > Policies > Admin Temps > Win Comps > Win Powershell > Turn on script execution > Not configured
- gpupdate /force
Powershell Basics
https://www.udemy.com/course/active-directory-group-policy-2012/learn/lecture/8472356#content
Focus on Powershell with Active Directory
Attributes
This isn’t a PowerShell command, but these will be used with many of the commands.
- AD > View > Advanced Features
- AD > … > Find Object (user, whatever) [RtClk] > Properties
- Open ‘Attribute Editor’ tab
Even Better:
Get-Help Set-ADUser
Commands
CLS
- Clear Screen
Get-ADUser
- Display information about the user including basic attributes
GetADUser -Identity ‘LoginName’
GetADUser -Filter {Attribute -eq ‘value’}
GetADUser -Identity ‘LoginName’ -Properties <attribute1 attribute2 …>
- Includes these attributes in the returned list.
Get-Alias
- Displays command aliases, such as ‘cls -> Clear-Host’
Get-Command *-AD*
- Displays all commands available in PS for AD
Get-Help command
- Help
Get-History
- View last ‘handfull’ of commands executed
Import-Module ActiveDirectory
- Run this if your AD command are not available
Set-ADUser “sAMAccountName” -Attribute “New Value”
Set-ADUser "sales" -EmailAddress "sales@domain.tld" # Alternative to set the 'Identity' but my test showed this was not needed. Set-ADUser -Identity "sales" ..
Start-Transcripit
- Stores commands in history. Will display the file path
- Good idea to run this as soon as you start Powershell
Keyboard Shortcuts
Up/Down arrows
- Scroll through previous commands
Tab
- Linux Auto-Complete
- Keep pressing tab to get all available commands
Variables
$MyVariable = 15 echo $MyVariable 15
36: Listing AD Users with Powershell
https://www.udemy.com/course/active-directory-group-policy-2012/learn/lecture/8287286#content
Display all users
# Import the active directory module Import-Module ActiveDirectory # List all AD Users & limit to 100 users Get-ADUser -Filter * -ResultSetSize 100
Display just names by piping through Select-Object
Get-ADUser -Filter * -ResultSetSize 100 | Select-Object Name Name ---- Administrator Guest krbtgt Thomas Roberts Sales Guy Engineering Guy
Display Multiple Attributes
Get-ADUser -Filter * -ResultSetSize 100 | Select-Object Name, UserPrincipalName, Enabled Name UserPrincipalName Enabled ---- ----------------- ------- Administrator True Guest False krbtgt False Thomas Roberts thomas@tas.local True Sales Guy sales@tas.local True Engineering Guy engineering@tas.local True
Additional Attributes
Get-ADUser -Filter * -ResultSetSize 100 -Properties lastLogon | Select-Object Name, UserPrincipalName, Enabled, lastLogon Name UserPrincipalName Enabled LastLogon ---- ----------------- ------- --------- Administrator True 132328447195664590 Guest False 0 krbtgt False 0 Thomas Roberts thomas@tas.local True 132328333914902895 Sales Guy sales@tas.local True 132327158751384175 Engineering Guy engineering@tas.local True 132328334198648061
Get all users from a specific OU
Get-ADUser -Filter * -SearchBase “LDAP_PATH”
Get-ADUser -Filter * -SearchBase "OU=Domain Users,OU=tas,DC=tas,DC=local" | Select-Object Name Name ---- Administrator Sales Guy Engineering Guy Thomas Roberts
To get the Ldap path to the ‘Domain Users’ OU:
Using Powershell (hard way)
PS C:\> cd AD: PS AD:\> dir Name ObjectClass DistinguishedName ---- ----------- ----------------- tas domainDNS DC=tas,DC=local Configuration configuration CN=Configuration,DC=tas,DC=local Schema dMD CN=Schema,CN=Configuration,DC=tas,DC=local DomainDnsZones domainDNS DC=DomainDnsZones,DC=tas,DC=local ForestDnsZones domainDNS DC=ForestDnsZones,DC=tas,DC=local PS AD:\> cd '.\DC=tas,DC=local' PS AD:\DC=tas,DC=local> dir Name ObjectClass DistinguishedName ---- ----------- ----------------- Builtin builtinDomain CN=Builtin,DC=tas,DC=local Computers container CN=Computers,DC=tas,DC=local Domain Controllers organizationalUnit OU=Domain Controllers,DC=tas,DC=local ForeignSecurityPr... container CN=ForeignSecurityPrincipals,DC=tas,DC=local Infrastructure infrastructureUpdate CN=Infrastructure,DC=tas,DC=local Keys container CN=Keys,DC=tas,DC=local LostAndFound lostAndFound CN=LostAndFound,DC=tas,DC=local Managed Service A... container CN=Managed Service Accounts,DC=tas,DC=local NTDS Quotas msDS-QuotaContainer CN=NTDS Quotas,DC=tas,DC=local Program Data container CN=Program Data,DC=tas,DC=local System container CN=System,DC=tas,DC=local tas organizationalUnit OU=tas,DC=tas,DC=local Test OU organizationalUnit OU=Test OU,DC=tas,DC=local TPM Devices msTPM-Information... CN=TPM Devices,DC=tas,DC=local Users container CN=Users,DC=tas,DC=local PS AD:\...> cd OU=tas PS AD:\OU=tas, DC=tas,DC=local> dir Name ObjectClass DistinguishedName ---- ----------- ----------------- Disabled Users organizationalUnit OU=Disabled Users,OU=tas,DC=tas,DC=local Domain Computers organizationalUnit OU=Domain Computers,OU=tas,DC=tas,DC=local Domain Groups organizationalUnit OU=Domain Groups,OU=tas,DC=tas,DC=local Domain Users organizationalUnit OU=Domain Users,OU=tas,DC=tas,DC=local Engineering$ volume CN=Engineering$,OU=tas,DC=tas,DC=local Sales$ volume CN=Sales$,OU=tas,DC=tas,DC=local Test no inherit organizationalUnit OU=Test no inherit,OU=tas,DC=tas,DC=local PS AD:\OU=tas,DC=tas,DC=local> cd '.\OU=Domain Users' PS AD:\OU=Domain Users,OU=tas,DC=tas,DC=local> # This is the ldap path!
ldap path = “OU=Domain Users,OU=tas,DC=tas,DC=local”
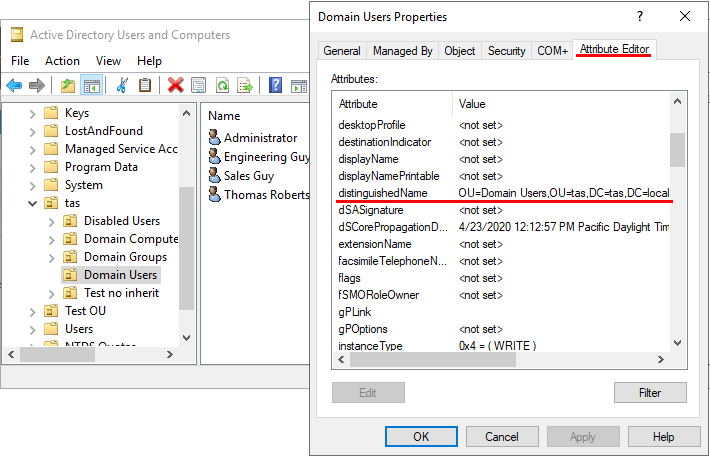
Using AD (Easy Way)
- AD > View > Advanced Features
- AD > … > Domain Users [RtClk] > Properties > Attribute Editor > distinguishedName
List all group members of a Security Group
Get-ADGroupMember 'SecurityGroupName' | Select-Object Name, DistinguishedName
List all Disabled accounts
Search-ADAccount -AccountDisabled
Export Any Output to a .CSV
Get-ADUser -Filter * -SearchBase "OU=Domain Users,OU=tas,DC=tas,DC=local" | Select-Object Name | Export-Csv "C:\Domain Users.csv"
37: Configure User Roaming Profile Path with Powershell
https://www.udemy.com/course/active-directory-group-policy-2012/learn/lecture/8414098#content
Create a script that sets the Profile Path for all users in the Roaming Profiles group
# Import the active directory module
Import-Module ActiveDirectory
# Get all members of the Roaming Profiles Group
Get-ADGroupMember 'Roaming Profile Users' |
# Loop through each user
ForEach-Object {
# Do this for each member
# $_ = Current Object
Set-ADUser $_.SamAccountName -ProfilePath ("\\WINAD01\Profiles$\" + $_.SamAccountName)
}
38: Creating User Accounts with Powershell
https://www.udemy.com/course/active-directory-group-policy-2012/learn/lecture/8287270#content
HInt:
- get-help new-aduser
- Boolean True / False must be set to 1 / 0
- Default ‘Enabled’ is False
# Import the active directory module
Import-Module ActiveDirectory
# You will need the distinguish name of the "Domain Users" OU for the user's path
New-ADUser `
-Name "Chucky Cheese" `
-GivenName "Chucky" `
-SurName "Cheese" `
-SamAccountName "ccheese" `
-AccountPassword (ConvertTo-SecureString "Password1234" -AsPlainText -Force) `
-Path "OU=Domain Users,OU=tas,DC=tas,DC=local" `
-ChangePasswordAtLogon 1 `
-Enabled 1
Running the script and enter the details at run time
# Import the active directory module
Import-Module ActiveDirectory
# Get the variables from the user
$firstName = Read-Host -Prompt "First name"
$lastName = Read-Host -Prompt "Last name"
$password = (ConvertTo-SecureString "Password1234" -AsPlainText -Force)
$path = "OU=Domain Users,OU=tas,DC=tas,DC=local"
# You will need the distinguish name of the "Domain Users" OU for the user's path
New-ADUser `
-Name "$firstName $lastName" `
-GivenName $firstName `
-SurName $lastName `
-SamAccountName "$firstName.$lastName" `
-AccountPassword $password `
-Path $path `
-ChangePasswordAtLogon 1 `
-Enabled 1
39: Creating User Accounts from a CSV File
https://www.udemy.com/course/active-directory-group-policy-2012/learn/lecture/8493210#content
Resource:
Code
# Import the active directory module
Import-Module ActiveDirectory
# Import users from .csv
$filepath = "C:\Users\Administator\Downloads\AD39-User-Accounts.csv"
# Import the csv into an array
$users = Import-CSV $filepath
# Setup some contants
$password = (ConvertTo-SecureString "Password1234" -AsPlainText -Force)
$path = "OU=Domain Users,OU=tas,DC=tas,DC=local"
ForEach ($user in $users) {
# Do this for each user
echo ("Adding: " + $user.'First Name' + " " + $user.'Last Name')
New-ADUser `
-Name ($user.'First Name' + " " + $user.'Last Name') `
-GivenName $user.'First Name' `
-SurName $user.'Lirst Name' `
-SamAccountName ($user.'First Name' + "." + $user.'Last Name') `
-UserPrincipalName ($user.'First Name' + "." + $user.'Last Name') `
-Description $user.Description `
-EmailAddress $user."Email Address" `
-Title $user."Job Title" `
-OfficePhone $user."Office Phone" `
-AccountPassword $password `
-Path $path `
-ChangePasswordAtLogon 1 `
-Enabled ([System.Convert]::ToBoolean($user.Enabled))
}
40: Move All Disabled Users to ‘Disabled Users OU” with Powershell
This scrip also disables any accounts in the Disabled Users OU that have NOT been disabled.
https://www.udemy.com/course/active-directory-group-policy-2012/learn/lecture/8301949#content
# Import the active directory module
Import-Module ActiveDirectory
# List all disabled users
Search-ADAccount -AccountDisabled | Select-Object Name, DistinguishedName
$disabledOU = "OU=Disabled Users,OU=tas,DC=tas,DC=local"
# Move these users to the Diabled Users OU
# This also moves users already in the disabled account!
Search-ADAccount -AccountDisabled | Move-ADObject -TargetPath $disabledOU
#This filters these users out
Search-ADAccount -AccountDisabled |
Where {$_.DistinguishedName -notlike $disabledOU} |
Move-ADObject -TargetPath $disabledOU
# Disable any accounts in this path that have not been disabled
Get-ADUser -Filter {Enabled -eq $True} -SearchBase $disabledOU | Disable-ADAccount
41: How to create AD Accounts with duplicate names
https://www.udemy.com/course/active-directory-group-policy-2012/learn/lecture/8301949#content
- Use the original account creation script
- Create a function that checks if the acct. exists.
- If so, return the next index digit (t.roberts, t.roberts1, t.roberts2)
# Import the active directory module
Import-Module ActiveDirectory
# Import users from .csv
$filepath = "C:\scripts\UserAccounts.csv"
# Import the csv into an array
$users = Import-CSV $filepath
# Setup some contants
$password = (ConvertTo-SecureString "Password1234" -AsPlainText -Force)
$path = "OU=Domain Users,OU=tas,DC=tas,DC=local"
ForEach ($user in $users) {
# Do this for each user
echo ("Adding: " + $user.'First Name' + " " + $user.'Last Name')
$accountNumber = checkName($user.'First Name'[0] + $user.'Last Name')
$userName = ($user.'First Name'[0] + $user.'Last Name' + $accountNumber)
New-ADUser `
-Name ($user.'First Name' + " " + $user.'Last Name' + $accountNumber) `
-GivenName $user.'First Name' `
-SurName $user.'Lirst Name' `
-SamAccountName $userName `
-UserPrincipalName $userName `
-Description $user.Description `
-EmailAddress $user."Email Address" `
-Title $user."Job Title" `
-OfficePhone $user."Office Phone" `
-AccountPassword $password `
-Path $path `
-ChangePasswordAtLogon 1 `
-Enabled ([System.Convert]::ToBoolean($user.Enabled))
}
function checkName($username) {
$i = 1
if ( userNameTaken($username) -eq $True) {
while ( userNameTaken($username + $i) -eq $True) {
$i++
}
} else {
return ""
}
return $i
}
function userNameTaken($username) {
$testPrincipal = Get-ADUser -Filter { userPrincipalName -eq $username }
$testSamAcctName = Get-ADUser -Filter { samAccountName -eq $username }
if ( $testPrincipal -eq $Null -and $testSamAcctName -eq $Null) {
return $False
} else {
return $True
}
}