ALWAYS REMEMBER THIS –
To Pass This Test, Think As An IT Manager or Risk Assessment Consultant!
CBK – Common Body of Knowledge
S9 – The CIA Triad
The CIA Triad (aka AIC)
- Confidentiality
- Integrity
- Availability
- Uses
- IPS/IDS
- Patching
- Redundancy (HA / no single point of failure)
- SLAs
- Threats
- Malicious attacks (DDOS, etc)
- Application failures (bugs)
- Component failures (Hardware)
- Uses
Find the right balance of these three!
Opposite of CIA
- Disclosure
- Destruction
- Alteration
S10 – IAAA
- Identification
- Name, username, ID number,
- Authentication
- Type 1 – something you know
- Password, pass phrase, pin
- Type 2 – Something you have
- ID, passport, smart card, token, cookie
- Type 3 – something you are
- Biometrics (fingerprint, iris scan, facial geometry
- Type 4 – Somewhere you are
- IP/MAC Address
- Type 5 – Something you do
- Signature, pattern unlock
- Type 1 – something you know
- Authorization
- Access control models
- (more of this in domain 5)
- Accountability
- Auditing
Security Governance Principles
- Least Privilege
- Minimum access required to do your job
- Need to know
-
- If you have access, but do not need it, do not access it.
- If you do, there will be consequences
-
- Non-repudiation
- User cannot deny performing an action
- (Authentication and Integrity)
- User cannot deny performing an action
- Subject (Active)
- Usually user, could be software
- Subject manipulates an Object
- Object (Passive)
- Passive data (data, piece of paper)
- Manipulated by a Subject
Clearly Understand Subjects and Objects
S11 – Governance, Management, Standards and Frameworks
Governance vs Management
- Governance (C Level)
- Stakeholder needs/wants
- Set the direction
- Set Risk appetite – Aggressive, neutral, adverse
- Management
- How to get to destination
- Plan, build, monitor
- Risk tolerance
- Used for Exam
Security governance principles
Top-Down vs Bottom-Up
- Bottom-Up
- IT is seen as a nuisance and not a helper, ofthen change when breaches happen
- Top-Down
- IP leadership is on board with IT Security, they lead and set the direction
- Used for Exam
C-Level (Senior Leadership) – Ultimately Liable
- CEO (Often also president) top of the chain
- CSO Chief Security Officer
- Us
- CIO / CTO Chief Information Officer / Chief Technology Officer
- CFO
- Know these for Exam
Security Standards and Control Frameworks
- PCI-DSS
- Payment Card Industry Data Security Standard
- OCTAVE
- Operationally Critical Threat, Asset and Vulnerability Evaluation
- COBIT
- Control Objectives for Information and related technology
- Goals for IT. Stakeholder needs mapped down to IT
- COSO
- Committee of Sponsoring Organizations
- Goals for the entire organization
- ITIL
- Information Technology Infrastructure Library
- ITSM IT Service Management
- Not sure why this is under ITIL
- FRAP
- Facilitated Risk Analysis Process
ISO 27000 Series
- ISO 27001
- Establish, Implement, Control and Improvement of ISMS
- Uses PDCA (Plan, Do, Check, Act)
- ISO 27002
- From British Standard 7799, 1/2, ISO 17799
- Provides practical advice on how to implement security controls
- Has 10 domains it uses for ISMS (Information Security management Systems)
- ISO 27004
- Provides metrics for measuring the success of your ISMS
- How do you know what success looks like?
- ISO 27005
- Standards based approach to risk management
- ISO 27799
- Directives on how to protect PHI (Protected Health Information)
Defense in Depth
aka Layered Defense or Onion Defense
- Implement multiple overlapping security controls
- Applies to Physical and Logical controls
- to get to a server, multiple locked doors, guards, man traps
- to get to data, firewalls, routers, switches, application security
- No single security control secures an asset
- This improves Confidentiality, Integrity and Availability
S12 – Laws and Regulations
Legal and regulatory issues
- Criminal Law
- Society is the victim
- Proof: “Beyond shadow of a doubt”
- Incarceration, death, finantial fines
- Punish and Deter
- Civil Law (Tort Law)
- Individuals, groups or orgs are victims
- Proof: “majority of proof”
- Financial fines to “Compensate the victims”
- Administrative Law
- Laws enacted by government agencies
- FDA, HIPAA, FAA,etc
- Proof: “More likely than not”
- Laws enacted by government agencies
- Private Regulations
- Compliance required by contract
- PCI-DSS
- Compliance required by contract
Legal and Regulatory Issues
- Liability
- Who is ultimately liable? Senior Leadership
- This does not mean you are not liable!
- Who is accountable, to blamme or should pay?
- This does not mean you are not liable!
- Who is ultimately liable? Senior Leadership
- Due Diligence
- The research to build the IT Security architecture of the organization
- Best practices and common protection mechanisms
- Research new systems before implementing
- Due Care
- Prudent person rule: What would a prudent person do in this situation
- Prudence: The ability to govern and discipline oneself by the use of reason
- Implement IT Security architecture, keep systems patched
- If compromised, fix the system, notify affected users
- Follows Security Polices to the letter
- Prudent person rule: What would a prudent person do in this situation
- Negligence (and gross negligence)
- Opposite of Due Care
- If a system is compromised and you can prove you did Due Care, you are likely not liable
- if you did NOT do Due Care, you are most likely liable.
Types of Evidence
How evidence is handled is VERY important
- Real Evidence
- Tangible and physical objects in IT Security
- Hard disks, USB drives, Fake ID cards
- Not the data!
- Direct Evidence
- Testimony from a first hand witness
- What experienced with 5 senses
- Circumstantial
- Supports the facts of the case.
- Usually have more than one possible explanation
- Corroborative
- Also supports faces or elements of the case
- Supports other facts of the case
- You hit my green car, you have green paint on your bumper
- Hearsay
- Not first-hand knowledge – normally inadmissible in a case
- At one time, computer generated records were considered Hearsay.
- Rule 803: Now admissible if record or report was made at or near time by or fron information transmitted by someone with knowledge…
- Tangible and physical objects in IT Security
Evidence Rules
- Best Evidence
- Accurate, Complete, Relevant, Authentic and Convincing
- Secondary
- Usually common involving IT
- Logs and documents from the systems
- Evidence Integrity
- It is important that the integrity of the evidence cannot be questioned!
- Use Hashes. All forensics are done on copies and never the originals
- Check hash against original and copy before and after forensics
- Chain of custody for original
- Who handled it?
- What did they do with it?
- Where did they handle it?
- When did they handle it?
Understand Local Laws (US)
Reasonable Searches
- 4th Amendment to US Constitution protects from unreasonable search and seizures by the government
- Courts will determine if evidence obtained legally, if not, inadmissible.
- Exigent circumstances apply if there is an immediate threat to human life or evidence destruction.
- Org must be very careful to ensure employees are aware in advance actions/devices are monitored.
- Org must also have a Security Policy in place before making notifications.
- If not informed, you cannot use it against them.
- Even if they agree, you must still obey local laws!
Entrapment
- Illegal and unethical
- Persuade someone to commit a crime they had no intention of committing
- Openly advertise sensitive data then charge them when they view it.
- Persuade someone to commit a crime they had no intention of committing
- Entrapment is solid legal defense
Enticement
- Legal and Ethical
- Making committing a crime more enticing
- Person has already committed a crime or has decided to do so.
- Honeypots are good way to use Enticement
- False networks
- Have open ports or services that can be attacked
- Enticement is NOT a valid defense
S13 – Intellectual property
Just need an overview
Types of Intellectual Properties
- Copyright
- Books, art, music, software
- If someone buys a copy of it, they have the right to sell it, but only once.
- Automatically granted
- 70 years after death
- 95 years after creation for corporations
- Books, art, music, software
- Trademarks and Registered Trademarks
- Brand Names, logos, slogans
- Must be registered
- Valid for 10 years at a time
- Can be renewed indefinitely
- Patents
- Protected inventions
- Novel (New idea no one has had before
- Useful – actually possible to use and is useful to someone
- Nonobvious – Inventive work involved
- Crytographic Algorithms CAN be protected! <- Exam
- 20 years normally
- Protected inventions
- Trade Secrets
- No protection
- Don’t tell anyone your “secret sause”. Once it’s out, you’re out of luck.
Attacks against Intellectual Property
- Copyright
- Piracy
- Software, Music, Movies
- Copyright infringement
- Use of someone else’s copyrighted material, often songs and images
- Piracy
- Trademarks
- Counterfeiting
- Fake Rolex, Nike, Apple, either using the real name or something very similar
- Counterfeiting
- Patents
- Patent Infringement – using someone else’s patent in your product without permission
- Trade Secrets
- Nothing you can do if discovered, but HOW it is discovered might be illegal.
- Cyber-Squatting
- buying a URL you know someone will need. NOT Illegal
- Typo Squatting
- Buying a URL that is VERY close to a real website name.
- MIGHT be illegal in certain circumstances
- If you’re not pretending to be the real website, OK.
- If you’re trying to trick people, it is illegal
S14 – US Laws, European laws and International treaties
Personally Identifiable Information – PII
- US Privacy regulation is a patchwork of laws. Some overlapping and some areas with no real protection
- More business friendly than EU
- EU Law – Very pro-privacy, strict protection on what is gather and how used, stored
- Many lawsuits against large corporations such as Google, Apple, Microsoft, etc.
US Rules and Regulations you should know
HIPAA: Health Insurance Portability and Accountability Act
- Privacy and Security on Personal Health Information (PHI)
- Privacy rule
- Security rule
- Breach Notification rule
- Administrative, Physical and Technical safeguards
- Risk Analysis required
Security Breach Notification Laws
- Not Federal, but 48 states have individual laws
- None in Alabama and South Dakota
- Generally require organizations to inform persons who have had their PII compromised
- Many have encryption clause
- If stolen/lost data encrypted, may not require disclosure
Electronic Communications Privacy Act ECPA
- Protection of electronic communications against warrantless wiretapping
- Weakened by the Patriot Act
Patriot Act of 2001
- Expands law enforcement electronic monitoring capabilities
- Allows search and seizure without immediate disclosure
Computer Fraud and Abuse Act (CFAA)
- Title 18 Section 1030
- Most commonly used to prosecute computer crimes
- Enacted in 1986, amended in
Gramm-Leach-Bliley Act (GLBA)
- Applies to financial institutions, enforced by several agencies (FDIC, etc)
- Requires protection of the confidentiality and integrity of consumer financial information
Sarbanes-Oxley Act of 2002 (SOX)
- Related to accounting scandals of late 1990’s
- Mostly for publicly traded companies
PCI-DSS
- Not a law – created by payment card industry
- Requires merchants and others to meet a minimum set of security requirements
- Mandates security policy, devices and control techniques and monitoring
EU Data Protection Directives
- Very Aggressive pro-privacy law
- Organization must notify individuals of how their data is gathered and used
- Orgainziations must allow for opt-out for sharing with 3rd parties
- Ot-in is required for sharing “most” sensitive data
- No transmission out of EU unless the receiving country is pre eived to have adequate (equal) privacy protections
- The US does NOT meet this standard.
- EU-US Safe Harbor optional between organizations and EU but this has been overturned! (Thanks Google and Facebook!)
International Guidelines
Organization for Economic Cooperation and Development OECD
- 30 worldwide members including US
- OECD guidelines (not required, just suggestions) on protection of privary and transborder flows of personal data
- 8 driving priniciples
- Collection limiting: Collection should be limited, obtained by lawful and fair means and with knowledge of the subject.
- Data quality: Personal data should be kept complete and current, and relevant to the purposes they are being used
- Purpose specification: Subjects should be notified for the reason for the collection at the time it is collected. Orgs should use it ONLY for that stated purpose
- Use Limitation: Only with consent of the subject, or by authority of law should the data be disclosed, made available, or used for purposes other than those previously stated.
Wassenaar Arrangement
- Originally for export/import controls for Conventional Arms and Dual Use goods and tecnologies
- 41 Countries
- Cryptography is considered “Dual Use”
- Iran, iraq, China, Russia and others have import restrictions on strong cryptography
- It can’t be so strong that it cannot be broken. They want to spy on their citizens
- Companies have to make “country specific” products with different encryption standards
- Arrangement is used both to limit what countries want to exprot and what some want to import.
- Responsibility of the Org to know what is permitted to import/export from and to a certain country
- 10 categories
- Special materials and related equipment
- Materials processing
- Electronics
- Computers
- Telecommunications
- Information security
- Sensors and Lasers
- Navigation and avionics
- Marin
- Aerospace and propulsion
3rd Party Acquisitions and Divesture Security
- As Orgs rely more on 3rd party vendors for services and appls, we need to ensure their security standards, mesures and controls meet the security stands of our Orgs.
- Procurement
- When you buy products or services from a 3rd party, security is included and not an afterthought
- A common agreement is an SLA (Service Level Agreement), for instance where a 99.9% uptime is promised.
- Industry Standard Attestation should be used
- 3rd party vendor must be accredited to the standards of your industry. This could be ISO, SOC, PCI-DSS
- “Rights to Pen Test” and “Rights to Audit” are often part of the agreement (clearly defined)
- Acquisitions
- Your Org has acquired another
- How do you ensure their security standards are high enough? how do you ensure data availability in the transition?
- Divestures
- Your Org is being split up
- How do you ensure no data crosses boundaries it shouldn’t?
- Who gets the IT infrastructure?
S15 – GDPR General Data Protection Regulation
GDPR Overview
- GDPR is a regulation in EU Law on data protection and privacy for all individuals within the EU and EU Economic Area (EEA)
- Does not matter where we are based. If we have customer in EU/EEA, me have to adhere to the GDPR
- Even if you are NOT in the EU, but are From the EU, you are covered.
- Violators of the GDPR may be fined up to 20 Million Euros or up to 4% of the annual worldwide turnover of the preceding finacial year in case of an enterprise, whichever is greater.
- Unless a data subject has provided information consent to data processing for one or more purposes, personal data may not be processed unless there is at least one legal basis to do so
- Does not matter where we are based. If we have customer in EU/EEA, me have to adhere to the GDPR
- Restrictions
- Lawful interception, national security, military, police, justice
- Personal Data
- Anything that can be used to identify a person
- Covers a variety of data types, including: Names, Email Addresses, Addresses, unsubscribe confirmation URLs that contain email and or names, IP Addresses
- Right To Request
- If someone controls your data, you have the right to request a free copy.
- Right to Erasure
- All users have a ‘right to be forgotten’.
- Unless they are required to keep it by law.
- Data Portability
- All users will be able to request access to their data in an electronic format
- Data breach notification
- Users and dat a controllers must be notified of data breaches within 72 hours
- Privacy by design
- when designed data processes, care must be taken to ensure personal data is secure. companies must ensure that only data is ‘absolutely necessary for the completion of duties’
- Data protection officers
- Companies whose activities involve data processing and monitoring must appoint a data protection officer.
- Someone directly responsible that you follow GDPR
S16 – Ethics
EXAM!
ISC2 Code of Ethics
Know both the preamble and canons for exam!
International Information System Security Certification Consortium
Basics
- You must agree to this before the exam
- It is very testable
- 4 mandatory canons in the code. Such high-level guidance is not intended to be a substitute for the ethical judgment of the professional
Preamble
- The safety and welfare of society and the common good, duty to our principles, and to each other, requires that we adhere, and be seen to adhere, to the highest ethical standards of behavior.
- Therefore, strict adherence to this code is a condition of certification.
Canons
- Protect society, the common good, necessary public trust and confidence, and the infrastructure.
- Act honorably, honestly, justly, responsibly and legally.
- Provide diligent and competent service to principles.
- Advance and protect the profession.
10 Commandments from Computer Ethics Institute
Have a good understanding of the intent behind these for exam.
Thou shalt not:
- Use a computer to harm other people
- Interfere with other peoples’ computer work
- Snoop around in other peoples’ computer files
- Use a computer to steal
- Use a computer to bear false witness
- Copy or use proprietary software for which you have not paid
- Use other peoples’ computer resources without authorization or proper compensation.
- Appropriate other people’ intellectual output
Thou shalt:
- Think about the social consequences of the program you are writing or the system you are designing.
- Always use a computer in ways that ensure consideration and respect for your fellow humans.
IAB’s (Internet Architecture Board) Ethics and the Internet
- Designed as a Request for Comment (RFC) #1087, published in 1987
- Considered unethical behavior
- Seeks to gain unauthorized access to the resources of the Internet
- Disrupts the intended use of the Internet
- Wastes resources (people, capacity, computer) though such action as
- Destroys the integrity of computer based information
- Compromises the privacy of users.
Your Organizations Ethics
- You need to know the Internal Code of Ethics of your organization
- If you don’t, how can you adhere to it??
- Usually very similar to that of the ISC2
- Do what is right
- Don’t steal
- Be ethical
S17 – Policies, Procedures, Guidelines and Frameworks
Information Security Governance
- Policies – Mandatory
- High-level, non-specific
- Can contain keywrods such as “Patches, updates, strong encryption”
- Will not be specific to OS, encryption type, vendor technologies
- Standards – Mandatory
- This is where we come in. Exam
- Describe specific uses of technologies
- All laptops are W10, 64 bit, 8 GB RAM, etc.
- Guidelines – Non-mandatory
- Recommendations, discretionary – Suggestions on how you would do it
- Procedures – Mandatory
- Low level, step-by-step guides, very specific
- They will contain OS, encryption type, vendor technologies
- Baselines (Benchmarks) – Non-mandatory
- Benchmarks for server hardening
- You can ignore the Benchmark as long as your server is as or more secure
Personnel Security
Users often pose the largest security risk!
- Awareness
- Change user behavior. This is what we want and we want them to change their behavior
- Training
- Provides users with a skillset. This only works if the user applies the knowledge.
- Employees need to want to want to learn, not want to because you tell them.
- Hiring practices
- Background checks for: references, degrees, employment, criminal, credit history
- New staff signs an NDA
- Vendors, Consultants and contractor security
- When using outside people in the environment, ensure they are trained how to handle data. Their systems must be secure enough to match the company policies and standards,
- Outsourcing and offshoring
- Can lower costs but requires a throrough and accurate Risk Analysis.
- Can also pose problems with them not having to comply with the same data protection standards
S18 – Access Controls
Access Control Categories
- Administrative
- Organizational policies and procedures
- Regulation
- Training and Awareness
- Technical
- Hardware/Software/firmware – Firewalls, routers, encryption
- Physical Controls
- Locks, fences, guards, dogs, gates, bollards
- Often used together with Technical controls
- Door with badge lock
Access Control Types
Exam, but somewhat self explanatory (more in Domain 5)
- Preventative – Prevents action from happening
- Least privilege access
- IPS (Intrusion Prevention)
- Firewalls
- Encryption
- Detective – Controls that detect during or after an attack
- IDS (Intrusion Detection)
- CCTV
- Alarms
- Anti-virus
- Corrective – Controls that correct an attack
- Anti-virus
- Patches
- IPS
- Recovery – Controls that help us recover after an attack
- Disaster recovery
- Backups
- HA
- Deterrents – Controls that deter an attack
- Fences
- Security guards
- Dogs
- Lights
- Beware of dog signs
- Compensating – Controls that compensate or assist other controls
- Other controls that are impossible or too costly to implement
S19 – Risk analysis, attackers and attacks
Risk Analysis
Qualitative vs. Quantitative
For any Risk Analysis, identify your assets. These are what you are protecting.
- Qualitative: Likelyhood
- Usually performed to assist Quantitative Analysis
- Vague, guessing, feelings, opinion
- How bad might it be if it does?
- See Risk Analysis Chart below
- Quantitative: What will the cost be if it does?
- Fact based analysis
- Cost of an asset, cost of a compromise…
- Threat: Potentially harmful incident
- Tsunami, Earthquake, Virus, Hack, …
- Vulnerability: Weakness that can allow the Threat to do harm
- Data center in flood area
- Earthquake zone
- Not applying patches and antivirus
- Not taking backups
- Risk: Threat x Vulnerability
- Impact: How bad it is (
- Total Risk: Threat x Vulnerability x Asset Value
- Residual Risk: Total Risk – Countermeasures
Exam Topic: Know difference between Threat and Vulnerability
- A Tsunami can be a Threat, but if your data center is in the mountains, it is not a vulnerability
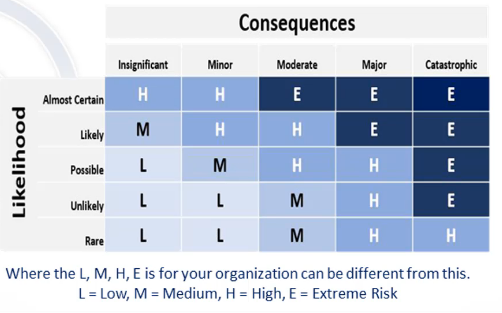
Risk Analysis Matrix
Qualitative Risk Analysis with Risk Analysis Matrix
- Pick an asset: A Laptop
- How likely it will be stolen or left somewhere
- Possible or likely
- How bad is it if that happens?
- Is it encrypted? Probably not too bad
- Does it contain classified PII/PHI content?
- Likely & Moderate = HIGH Risk
- How likely it will be stolen or left somewhere
- It is normal to move high and extreme to quantitative risk analysis
- If mitigation is implemented, perhaps move the risk level to Low or Medium
Quantitative Risk Analysis
We want exactly enough security for our needs. This is where we put a number on this.
Exam: Know these abbreviations
- Find an asset’s value
- How much of it is compromised?
- How much will one incident cost?
- How often might the incident occur?
- How much is all of this per year?
- Asset Value (AV): $ – How much is the asset worth?
- Exposure factor (EF): % – Percentage of Asset Value lost?
- Single Loss Expectancy (SLE): AV x EF
- Annual Rate of Occurrence (ARO): Quantity – How often per year if we do nothing
- Annualized Loss Expectancy (ALE): SLE x ARO How much it will cost per year if you do nothing
- Total Cost of Ownership (TCO): Mitigation cost: Upfront + ongoing cost (Normally Operational)
Example: Laptop
- AV: $10,000 ($1000 Cost + $9000 for data stored on it)
- EF: 100% (Going to lose entire value)
- SLE: $10,000
- ARO: 25 / Year
- ALE: $250,000
What if:
Calculate on a 4 year tech refresh cycle
- Implement encryption software and support
- $75,000 implementation
- $5,000 / year
- $95,000 over 4 years
- Remote data wipe
- $20,000 init
- $4,000 / year
- $36,000 over 4 years
- Staff
- $25,000 / year
- $100,000 over 4 years
- Cost / year: $57,750 (231,000/4)
- Cost to do nothing:
- Cannot protect loss of hardware, so can only include costs of data
- 25 x $9000 = $225,000 / year
- TCO for security: Save $225,000/yr by spending $57,750/yr.
- Sold!
Example: Data Center – Flooding
- AV: $10,000,000
- EF: 15%
- SLE: %1,500,000
- ARO: .25
- ALE: $375,000
Risk Analysis
- Accept the risk: If the cost to protect is not worth the cost to do nothing, do nothing and accept the risk.
- Make sure you have the paper trail to back up this decision!
- Mitigate the risk: Take measures as above for the laptop to reduce the loss
- Transfer the risk: For the Data Center, buy flood insurance.
- You’ll still lose 15% of your DC, but won’t have to pay for it!
- Risk Avoidance:
- Don’t issue laptops
- Don’t build in a flood plain
- Risk Rejection: You know the risk is there, but ignore it. NEVER Acceptable!
- Secondary Risk: Mitigating one risk may open another risk
- Upgrading software might open new can of worms
Qualitative: “Quality” Semi vague, e.g. “Pretty good quality”
Quantitative: “Quantity” Specific numbers
NIST 800-30 – Risk Analysis Framework
9 step program for Risk Management
United States National Institute of Standards and Technology Special Publication
- System Characterization
- Risk management scope
- Boundaries
- System and data sensitivity
- Threat Identification
- What are the threats to our systems?
- Vulnerability Identification
- What are the vulnerabilities of our systems?
- Control Analysis
- Analysis of the current and planned safeguards, controls and mitigations.
- Likelihood Determination
- Qualitative – How likely is this to happen?
- Impact Analysis
- Qualitative – How bad will it be if it does happen?
- Loss of CIA (Confidentiality, Integrity, Availability)
- Risk Determination
- Look at #5 and #6 and determine Risk and Associate Risk Levels
- Control Recommendations
- What can be done to mitigate, transfer, etc., the risk?
- Results Documentation
- Document with all facts and recommendations
It is our job to make the recommendations, not to implement them. How this document is used is up to Senior Management
Types of attackers:
- Hackers
- Now: Anyone trying to get access to, or disrupt an leg of the CIA Triad (Confidentiality, Integrity, Availability)
- Original use: Someone using something in a way not intended
- White Hat hackers: Professional Pen Test (penetration testing) trying to find flaws so we can fix it.
- aka Ethical Hackers
- Black Hat hackers: Malicious hackers, trying to find flaws to exploit them
- aka “Crackers”, they crack code
- Gray Hat hackers: Between Black and White hat hackers.
- Look for vulnerabilities and publish them, often before patches can be released.
- Sometimes will inform the company of the vulnerability and if the company does not fix, then they publish.
- Script Kiddies
- Little or no coding knowledge, but have sophisticated tools.
- Pose very real threat, just as dangerous as skilled hackers
- No clue what they are doing.
- Outsiders
- Unauthorized individuals -Trying to gain access, launch the majority of attacks, but are often mitigated if the organization has good Defense in Depth
- Interception, malicious code (virus, logic bomb, trojan horse), sale of PI, system bugs, system intrusion, sabotage or unauthorized system access
- 48- 62% of risks are from outsiders
- Insiders
- Authorized individuals – not necessarily to the compromised system, who intentionally or unintentionally compromise the system or data
- This could include: Assault on an employee, blackmail, browsing for proprietary information, computer abuse, fraud and theft, information bribery, input of falsified or corrupted data
- 38 – 52% of risks are from insiders
- Another reason good Authentication and Authorization controls are needed.
- Hacktivism / Hacktivist (Hacker Activist)
- Hacking for apolitical or socially motivated purposes
- Often aimed at free speech, human rights, etc.
- Famous attacks:
- Anonymous DDOS attack on Visa, Mastercard, PayPal to protest the arrest of Julian Assange (Wikileaks)
- Google/Twitter/SayNow worked together to provide communication for the Egyptian people when the government backed out the internet in 2011 protests
- Governments
- State sponsored hacking is common. If you see attacks happening between 9 – 5, this is a day job.
- Approx. 120 countries have been developing ways to use th einternet as a weapon to target financial markets, gov. computers systems and utilities.
- Famous attacks:
- US elections (Russia)
- Sony websites (N. Korea)
- Stuxnet (US/Israel)
- US office of Personnel Management (China)
- Bots and Botnets
- Bots
- Bots are a system with malware controlled by a botnet
- The system is compromised by an attack or the user installing a remote access trojan (game or application with a hidden payload)
- They often use IRC, Http or Https
- Some lie dormant until activated
- Others are actively sending data from the system (CC and Bank info)
- Can be used to send spam emails, DDOS, etc.
- Botnets
- Command and Control network, controlled by people (bot herders)
- There can be thousands or 10 of thousands of bots in a botnet.
- Bots
- Phishing
- Phishing
- Social engineering email attack
- Click to win, send information to get your inheritance
- Sent to hundreds of thousands of people. If only 0.02% follow the instructions, they have 200 victims
- A Public treasurer in Michigan send 1.2M to Nigeria (1.1 taxpayer funds, 72k of his own.)
- Spear Phishing
- Targeted phishing, not just random spam
- Sent with knowledge about the target. Familiarity increases success
- Whale Phishing (Whaling)
- Targeted toward senior leadership
- Your company is being sued.. fill out attached docs
- Targeted toward senior leadership
- Vishing (Voice Phishing)
- Attacks over automat6ed VOIP systems. Bulk spam similar to phishing
- Your taxes are overdue. Your account is locked. Enter your PII to prevent this.
- Phishing
S20 – Domain 1 Summary: Security and Risk Management
- How we want our data to be Confidential, keep its Integrity and have it Available when we need to access it. CIA
- How we Identify, Authenticate, Authorize our employees and keep them Accountable. IAAA (IAAA)
- Need to know, least privilege, non-repudiation, subjects and objects. Need to know
- The governance structure we have in our organization, control frameworks we use, how we use defense in depth. GOV
- Laws and regulations in our field and in general. LAWS
- How we use due care, due diligence to avoid negligence and who is liable when. DILIGENCE
- What constitutes evidence and how we collect and handle it properly. EVIDENCE
- The different kinds of intellectual property, the laws around them and attacks on them. Intellectual property
- The ISC2 code of ethics – Must agree to them before taking the exam and they are very testable. (ISC)2
- The qualitative risk analysis, that then leads into the quantitative risk analysis, where we put numbers and dollars on the risks and then chose mitigation strategies. Risk Analysis
- The attackers we need to protect ourselves against. Attackers